║┌┴Ž╩ėŲĄ for DevOps
║┌┴Ž╩ėŲĄ, a virtual private programmable network
Achieve connectivity across VPCs, clusters, and heterogeneous environments quickly.
Trusted by 10,000+ companies like these
Connect to VMs and containers via SSH

Never forget your (SSH) keys
Instead of self-managing or sharing keys across an entire fleet of machines, use ║┌┴Ž╩ėŲĄ SSH to automatically rotate SSH keys, while validating user identities against an existing IdP (e.g Google Workspace or Okta).
Say goodbye to open ports
║┌┴Ž╩ėŲĄ establishes end-to-end encrypted connections between any two devices on the internet without opening sensitive ports to the world, so go ahead and DROP all INPUTs.
SSH recording in 3, 2, 1ŌĆ” easy steps
Meet compliance obligations, or just debug what happened last week, with the ability to record and replay ║┌┴Ž╩ėŲĄ SSH sessions.
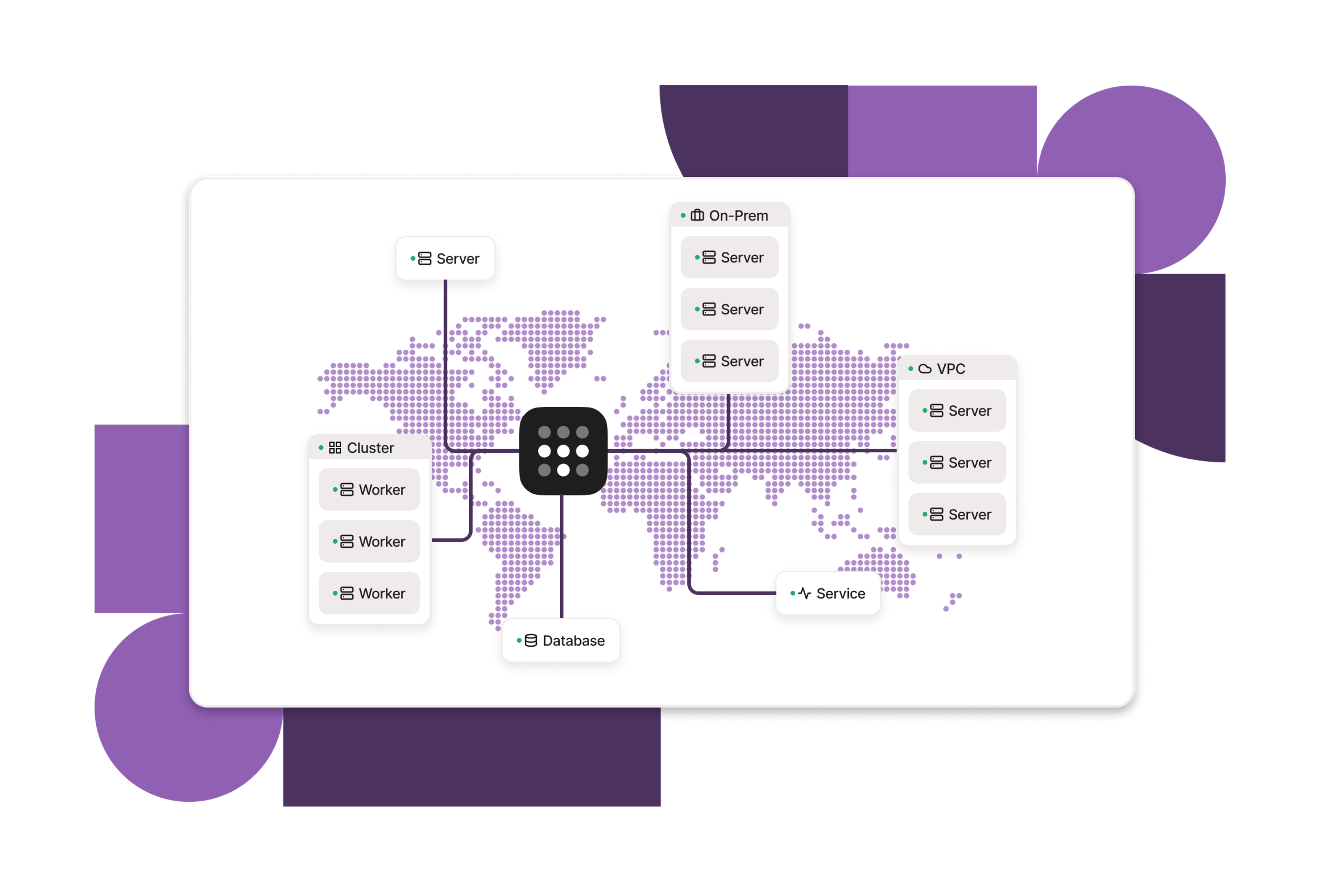
Connect Kubernetes Clusters
Bridge the Kubernetes network gap
Use ║┌┴Ž╩ėŲĄŌĆÖs operator to seamlessly connect clusters with other infrastructure, including: logging, CI / CD workflows, other internal APIs, and managed databases.
Any environment, tool, or team
Quickly enable secure access to dev, test, staging, and production environments. SCIM group sync and just-in-time access make it easy to provide the right access at the right time.
Keep clusters off the open internet
Connect a cluster with ║┌┴Ž╩ėŲĄ to drop the risky public IP for the control plane. With minimal configuration itŌĆÖs possible to securely manage & debug clusters from anywhere.
Webinar
Watch our webinar on using ║┌┴Ž╩ėŲĄ for Kubernetes networking
Find out how ║┌┴Ž╩ėŲĄ can make your your life with Kubernetes hassle-free.

Connect CI / CD Pipelines
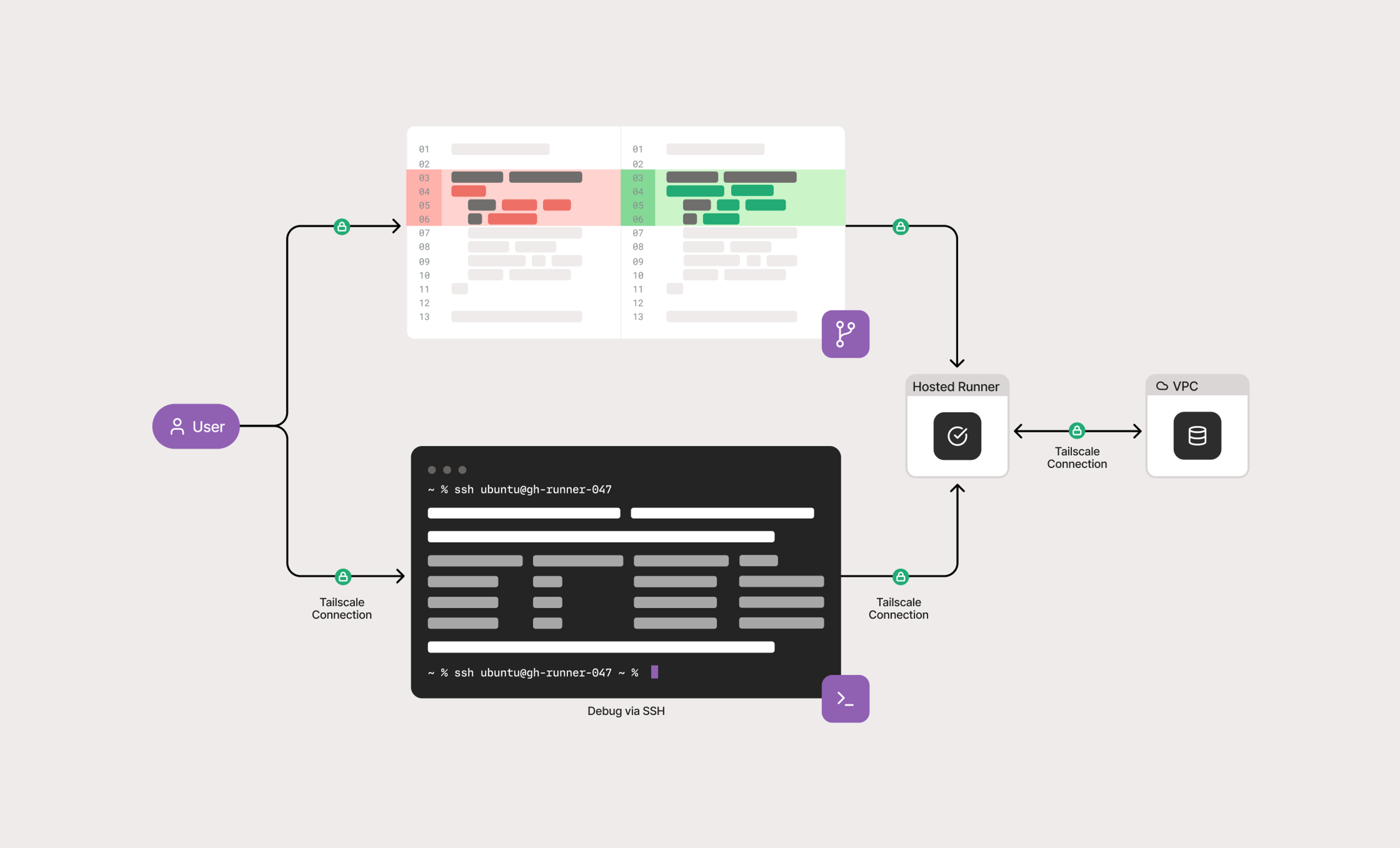
The key to fixing broken builds
SSH into CI / CD job runners to diagnose build issues without the complexity of managing or sharing keys. ║┌┴Ž╩ėŲĄ SSH takes all the hassle out of key management and easily integrates with existing identity providers.
Continuous meets connectivity
Easily & securely connect cloud or local CI / CD runners to internal services and test databases across clouds, VPCs, or regions.
A Network of Benefits
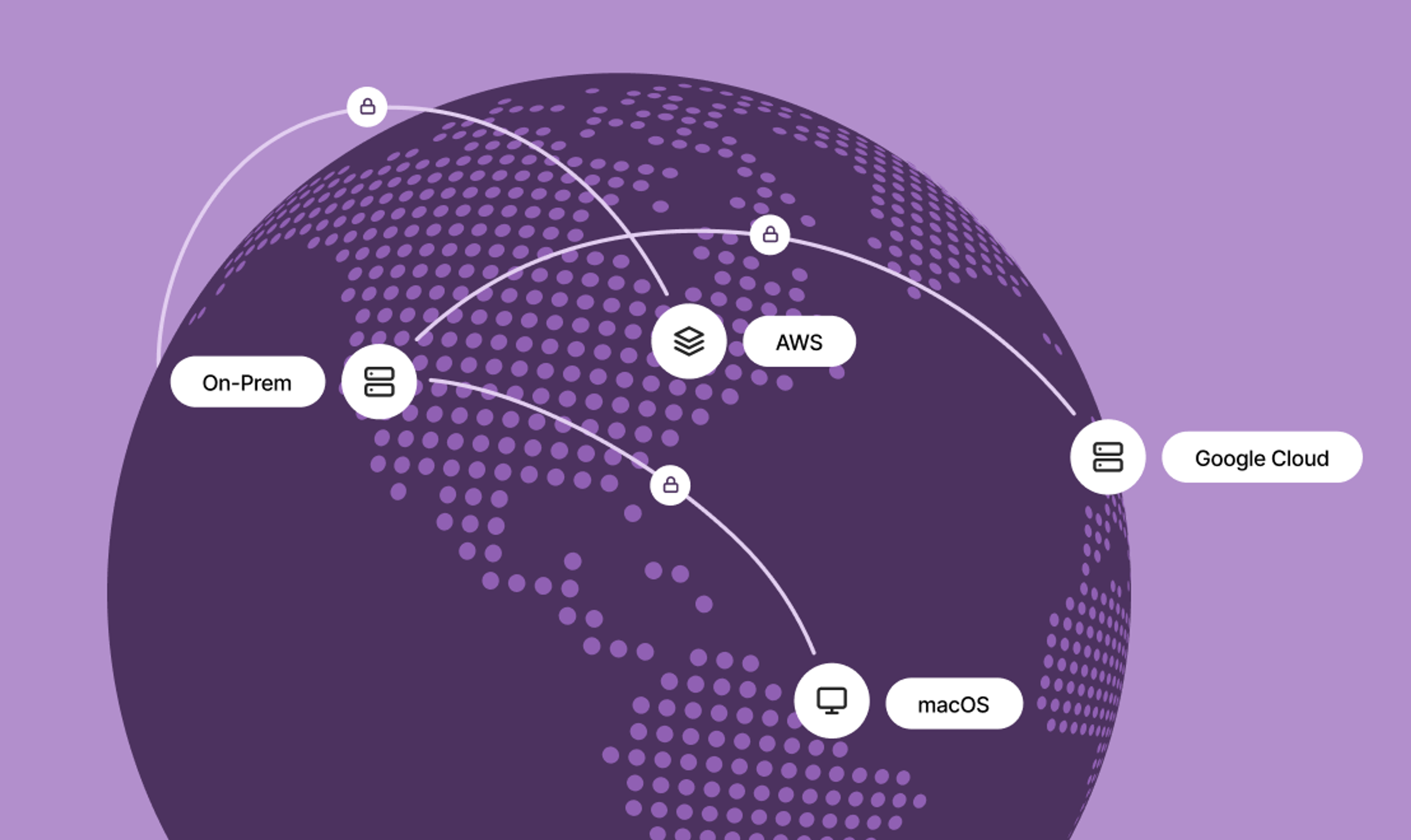
Unified Networking Across Any Infrastructure
Securely connect anything on the internet with ║┌┴Ž╩ėŲĄ. Create a unified, secure network that bridges all of your machines regardless of their physical location or the network topology between them.
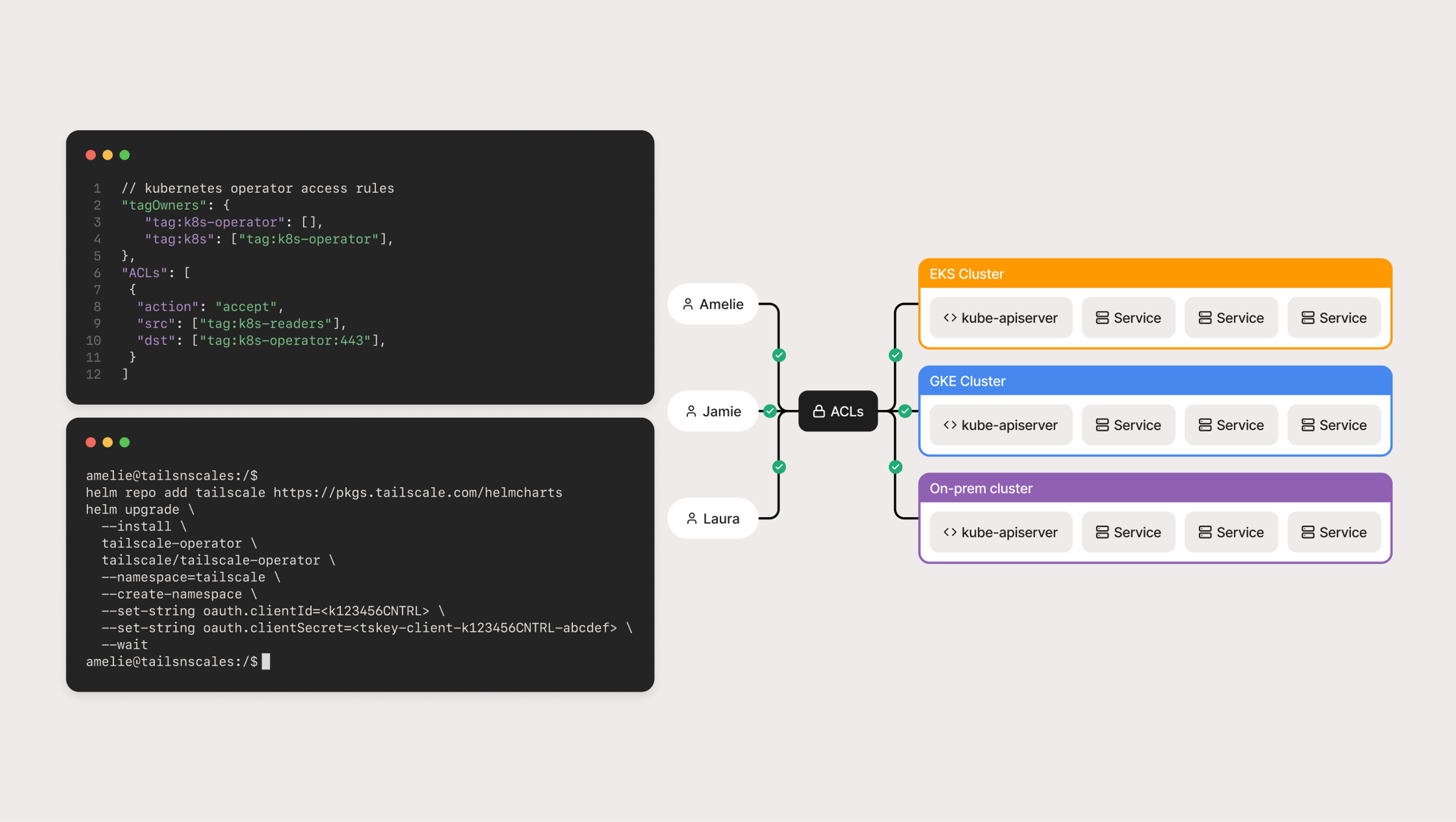
Simplified SSH User & Key Management
Use ║┌┴Ž╩ėŲĄŌĆÖs drop in SSH replacement to easily manage shell access to any linux based infrastructure. Verify user identities against an existing IdP (e.g Google Workspace or Okta) and manage access via centralized grants and access control lists (ACLs).
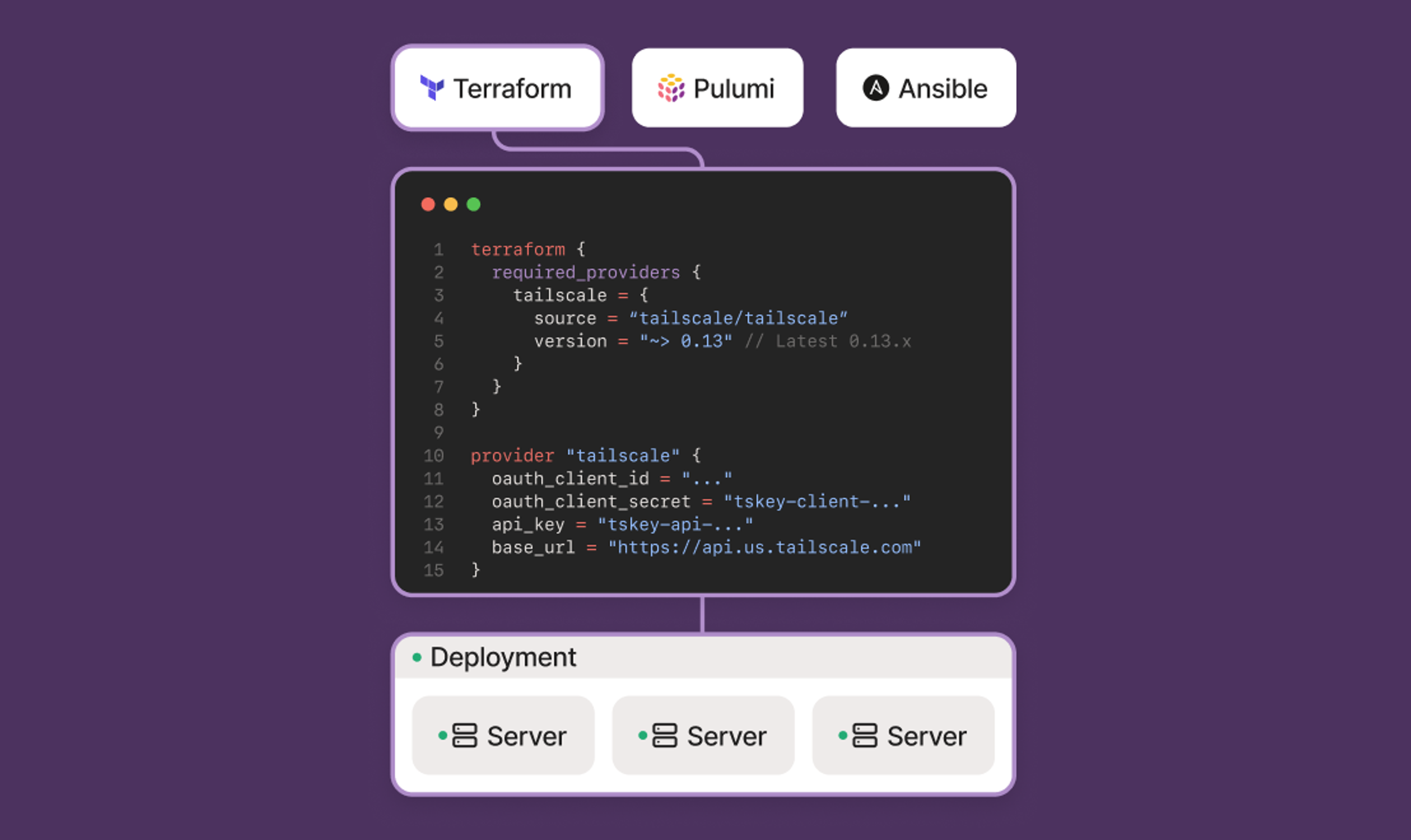
Automated Network Configuration & Deployment
║┌┴Ž╩ėŲĄ seamlessly integrates into any GitOps workflow with support for popular Infrastructure as Code (IaC) tools like Terraform, Pulumi, and Ansible. Using native integrations, both deployment and network access policies can be checked into version control for easy review and rollbacks.
Secure Network Access on Every Endpoint
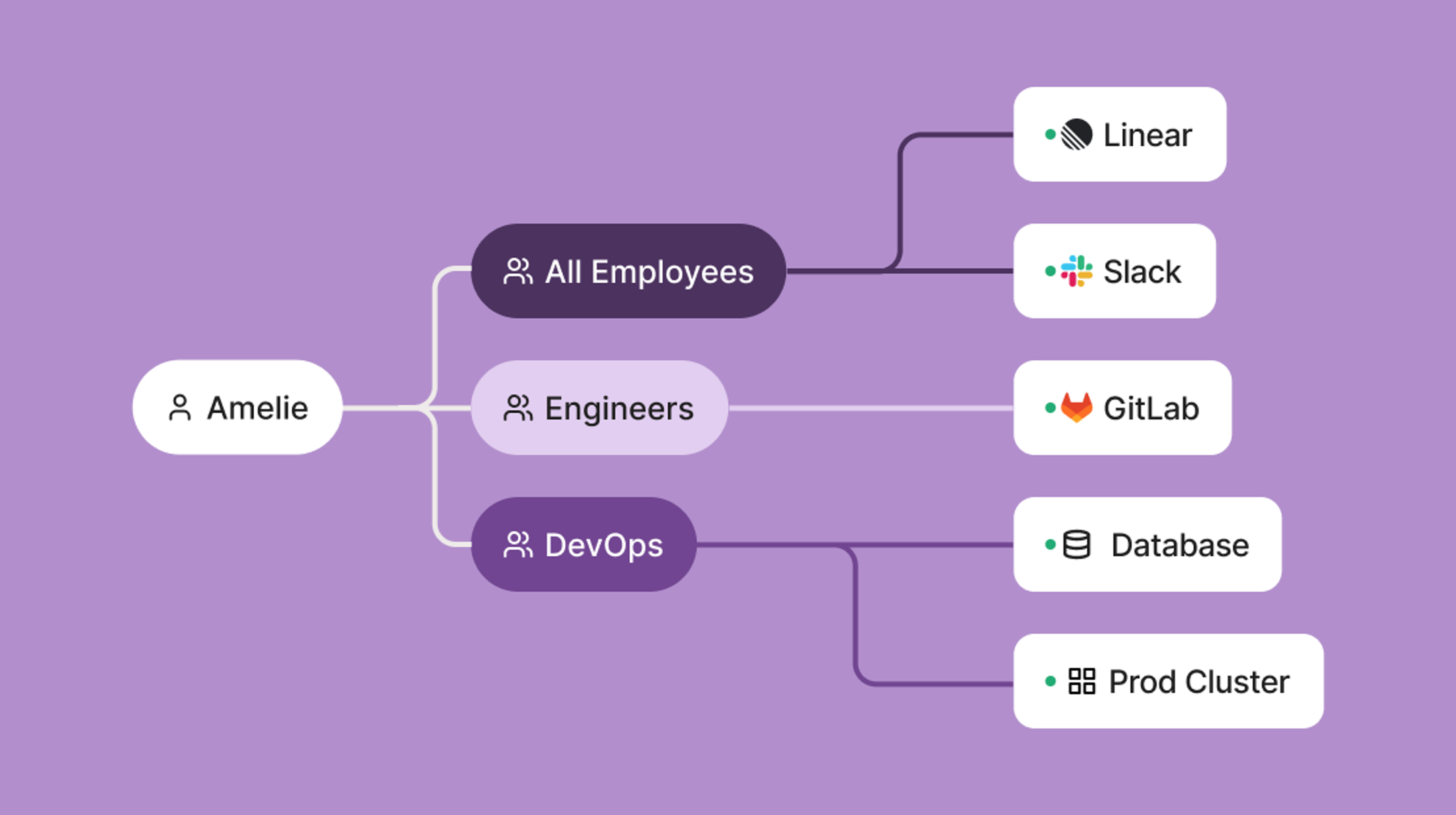
Easily install ║┌┴Ž╩ėŲĄ on every machine and in every cluster to enable authenticated & direct connections, encrypted end-to-end, between any two machines or users. Customize network access with fine-grained control based on user identity, source machine, and custom tags.
Get these features and more with ║┌┴Ž╩ėŲĄ
║┌┴Ž╩ėŲĄ SSH
Use this drop-in replacement to manage & record shell access into any linux machine without needing to share or manage keys.
Kubernetes Operator
Quickly route traffic to & from Kubernetes clusters to your Tailnet while keeping services and the control plane off the public internet.
Subnet Routers
Establish connectivity to entire VPCs or devices where ║┌┴Ž╩ėŲĄ can't be installed.
IaC Integrations
Easily deploy ║┌┴Ž╩ėŲĄ into cloud and on-prem environments via your IaC provider of choice, including: Terraform, Pulumi, and Ansible.
GitOps for ACLs
Easily modify and rollback JSON based network configuration directly from GitHub or GitLab.
║┌┴Ž╩ėŲĄ Serve
Quickly & securely share prototypes, demos, or web applications with other users on a Tailnet regardless of location or network.
End-to-end Encryption
By installing the ║┌┴Ž╩ėŲĄ client, all traffic is encrypted end-to-end using the Wireguard┬« protocol.
Bring your own IdP
Use SSO & MFA from a wide array of supported IdPs to authenticate users onto any Tailnet.
Log Streaming
Natively stream network flow and configuration audit logs to popular SIEM providers.
Pricing that works for everyone
For individuals who want to securely connect personal devices, for free.
For small teams seeking an easy-to-use and quick-to-deploy secure network access solution.
For growing teams seeking advanced service/resource-level networking and identity-aware access controls.
For organizations seeking advanced user and posture management, robust compliance, and dedicated support.
